
The Axiad Advantage
A Holistic Approach to Authentication
Axiad’s integrated approach to authentication delivers lower risk and less user friction than fragmented strategies


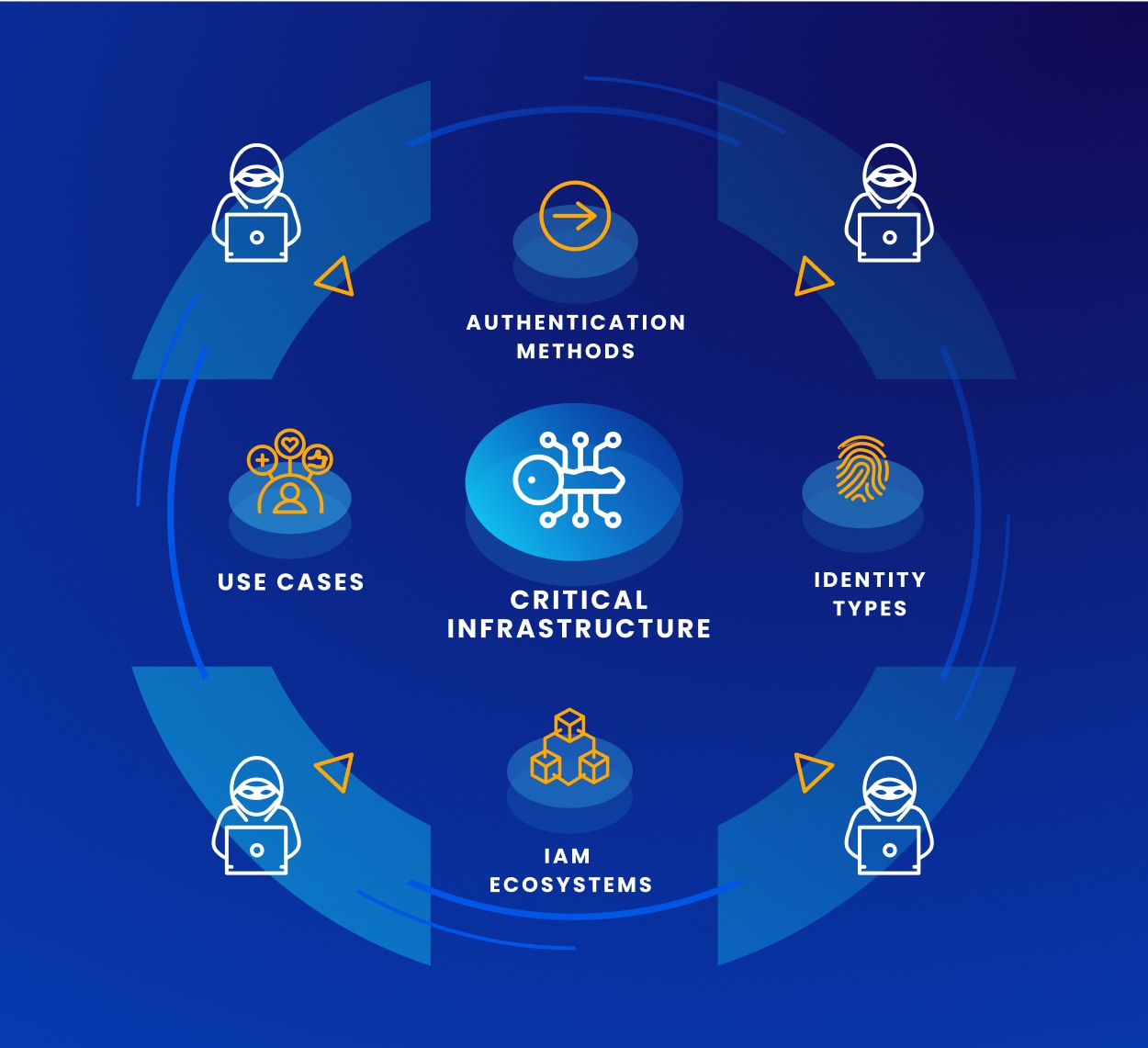
The Problem
Siloed Authentication Yields Material Risk
Many organizations leverage numerous authentication methods,
have multiple identity types to protect, must support a wide
range of use cases, and may already have existing IAM investments to consider. This complexity can force organizations to take a siloed approach to authentication, which can lead to gaps and inconsistencies that can be exploited by bad actors.
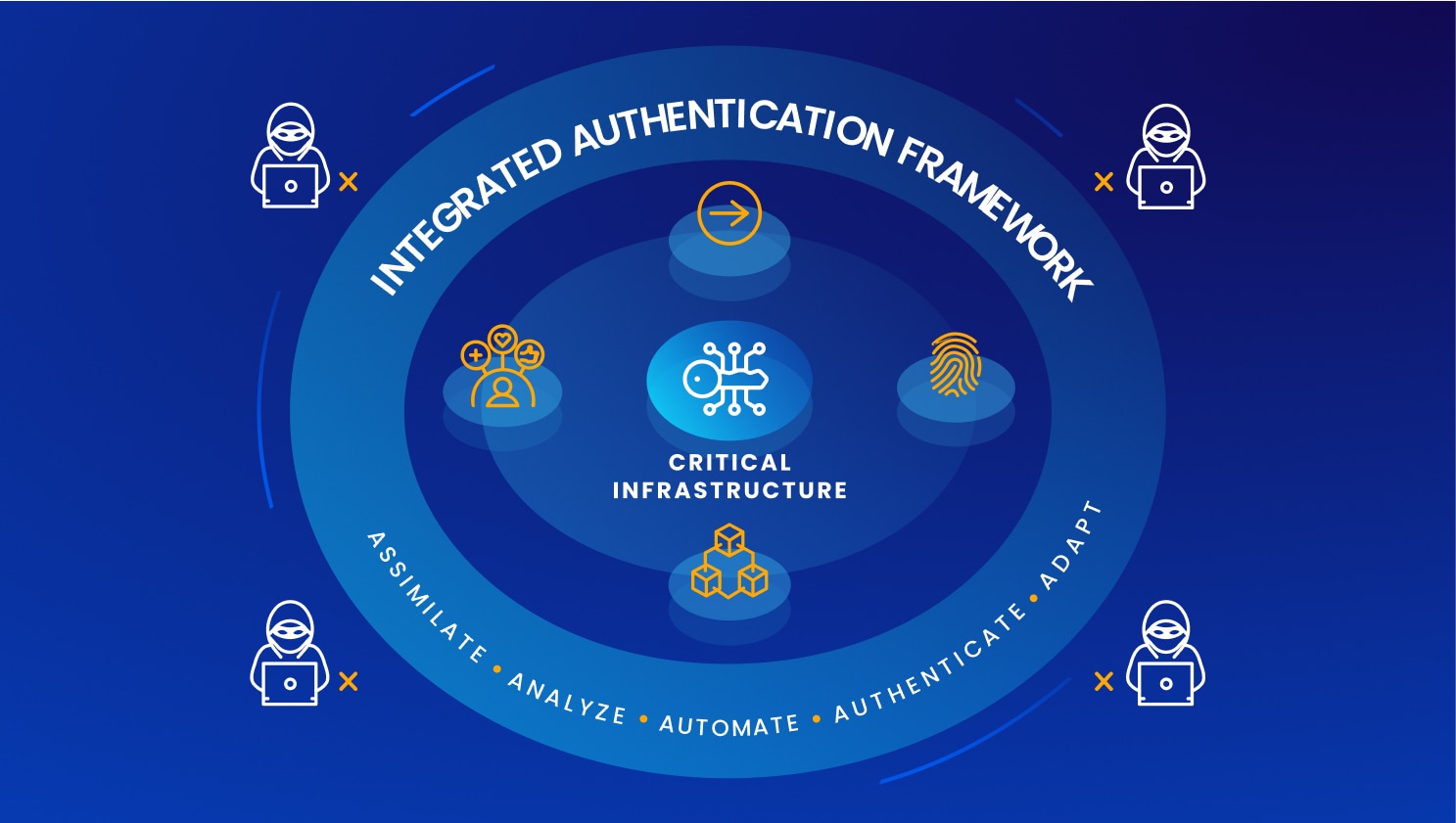
The Path Forward
A Holistic Approach Reduces Your Risk Exposure
Many organizations are shifting from a fragmented approach to a single, holistic strategy – an integrated authentication framework. This strategy allows security executives to assimilate credentials, analyze in context, automate processes, authenticate uniformly, and adapt to emerging threats more efficiently.
Key Outcomes Delivered
Operational and Security Benefits
Operational Benefit
Reach a balance between usability and protection
Employees can access what they need, when they need it, without friction, so they are more productive
Security Benefit
Fight back against a common form of attack
Resist attempts to compromise or subvert the authentication process by driving day-one enrollment and enforcing critical policies
Operational Benefit
Streamline key processes organization wide
Administrators and help-desk employees, who are already over subscribed, can do their jobs more efficiently
Security Benefit
Verify everything before granting access
Continuously authenticate ever user, every machine, and every digital interaction, as a critical element of a Zero Trust strategy

Our Core Differentiation
Organization-Wide Passwordless Orchestration
-
Holistic SolutionLeverage a single platform for all your user and machine authentication needs
-
Credential CentricEnsure there are no shared secrets that can be exploited behind the scenes
-
InteroperableFortify existing IAM investments instead of ripping and replacing tools that are working well
-
Optimally SecureRetain maximum control over the keys to the kingdom with no commingled credentials
-
Simple and AutomatedRemove friction from admin and users with high levels of orchestration
-
Future ProofedBuild a foundation for your IAM strategy that can easily adapt as your requirements evolve

Get Started Now
To learn more about how Axiad can help you shift from a fragmented to a holistic approach to authentication across the enterprise, we invite you to try us at no cost for 30 days.

